The following is inspired by the article from Kris the Coding Unicorn. This is not meant to be a comprehensive suite of tests but a start.
The following steps use the open-source Security Code Scan project, which publishes a tool to NuGet.
Unfortunately, Jenkins doesn’t seem to have a mechanism for visualizing security scans, so the output file is stored as an artifact of the job.
The security scan work can be done entirely within the Jenkinsfile.groovy. There are no additional Jenkins plugins or other components to install.
The security scan is just another block within the script. I’ve opted to make the tool local instead of global to avoid potential collisions with other jobs (a paranoia of mine).
With a previous cleanup iteration, we didn’t need to code to search for a solution anymore; however, that need has resurfaced, and the code is contained within the stage.
stage ("Run Security Scan") {
steps {
bat "dotnet new tool-manifest"
bat "dotnet tool install --local security-scan --no-cache"
script {
def slnFile = ""
// Search the repository for a file ending in .sln.
findFiles(glob: '**').each {
def path = it.toString();
if(path.toLowerCase().endsWith('.sln')) {
slnFile = path;
}
}
if(slnFile.length() == 0) {
throw new Exception('No solution files were found to build in the root of the git repository.')
}
bat """
dotnet security-scan ${slnFile} --excl-proj=**/*Test*/** -n --cwe --export=sast-report.sarif
"""
}
}
}
Because Jenkins doesn’t have a plugin to report the security issues yet, for now, we’ll attach the file as an artifact in the post section. In the future, we can emit more useful information about the reported security problems.
post {
always {
archiveArtifacts(artifacts: "sast-report.sarif", allowEmptyArchive: true, onlyIfSuccessful: false)
}
cleanup {
cleanWs(deleteDirs: true, disableDeferredWipeout: true, notFailBuild: true)
}
}
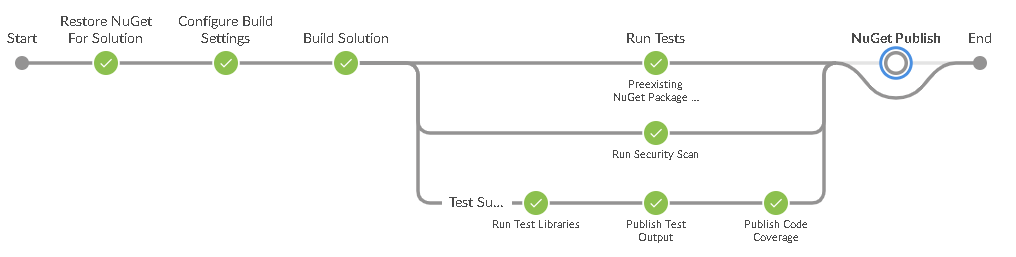
With the growing number of tests we are running, I have also altered the Jenkinsfile.groovy to parallelize the tests. I won’t go into detail here, it is essentially a parallel option that wraps the test stages to produce the output:

Pingback: CI/CD Log Processing | Brent Scriver